Traditionally, employees have shown up for work at 8 a.m. to work in an office for the next 8 or so hours.
But as technology advanced (high-speed Internet, at-home firewalls, laptops) office work was no longer restricted to happening in the four walls of your company’s building. Working remotely became a way for businesses to offer flexibility for some or all employees.
Since the coronavirus was declared a pandemic, the majority of businesses having pivoted to working remotely (all working non-essential employees), companies need to have the right tools to successfully set up their employees to work from home.
At The KR Group, we’ve been helping industries set up remote workforces even before working from home was the only option.
When it comes to setting up a remote workforce, we’ve always advised businesses to prioritize their remote needs in three areas:
- Connectivity
- Collaboration
- Security
Each of the three areas is vital to create a successful remote workforce that can continue your business’s operations from home.
Connectivity requirements for your remote workforce
Connectivity is the basis of setting up a remote workforce. Without connectivity, your users have no means to access files or applications to perform their jobs at home.
What do you need to consider for connectivity?

1. Work station
All of these tools won’t be helpful if your users don’t have an at-home workstation to use them on. For most employees, they’ll rely on a company-issued laptop to continue doing their jobs at home.
2. Secure Internet connection
At the most basic level, this means confirming each remote worker has an Internet connection. However, since they are no longer working on your company’s network, which you have control over, there are security precautions you need to take. We’ll discuss those in the section on security.
3. Adequate bandwidth
Not only do your users need a secure Internet connection, but you need to have enough bandwidth for your employees to all remotely access files and applications.
Adequate bandwidth varies based on user count, the type of applications your workforce uses, and where those applications are stored. The best way to ensure you have an adequate amount of bandwidth for your specific situation is to ask your IT consultant.
4. VPN connection
If you need to access corporate data on-premises hosted at your organization, each user will need a virtual private network (VPN) to provide a secure path for access.
5. Virtual desktop infrastructure (VDI) or remote desktop services (RDS)
Both VDI and RDS allow your remote users to access virtualized systems. Which one will work best for your business depends on your unique needs. Again, it is best to contact your IT consultant for the best match.
Collaboration requirements for your remote workforce
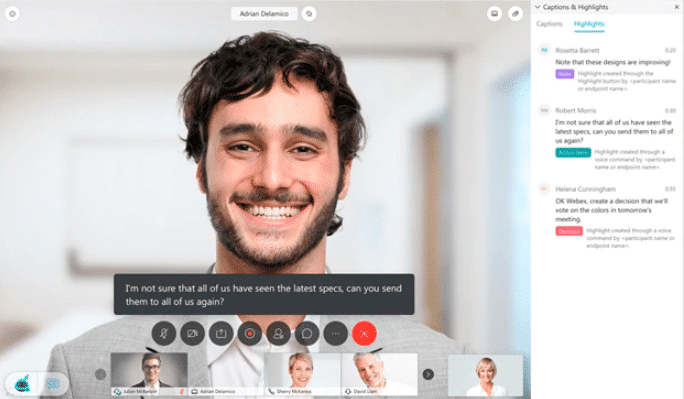
The key to staying connected to your employees and customers is collaboration – the sharing of audio, video, and content.
When you’re setting up remote employees, you’ll need to consider audio and video.
What do you need for audio and video collaboration?
Audio and video each require their own set of tools to work remotely, but there are a few things you’ll need for both.
1. Network and power for desk phones
For in-office use, most companies’ infrastructure is equipped with network cable management and Power over Ethernet (PoE) to power phones. However, most homes are not equipped to handle these requirements.
If your employees have designated home desk phones or video devices, you’ll need to ensure your employees can run a network cable from the firewall to the desk so they can connect and possibly power the desk phone.
2. Noise reduction applications
While not a necessity, noise reduction applications can help you or your employees if you’re working in a noisy environment (at home with children, for example) and trying to make or join audio or video calls.
What do you need for audio collaboration?
When it comes specifically to audio, there are three things you’ll need to implement to set up your remote workforce.
1. Extension forwarding
By setting up extension forwarding, your employees will continue to receive calls that would normally ring their office phones from their cell phone.
2. Softphones
An alternative to setting up physical desk phones or extension forwarding is licensing one of your user’s devices as a softphone.
3. Headsets
While not a necessity for your remote workforce, headsets are useful to block or cancel background noise that may be present at a home office, as well as use a microphone to pick up a clear signal to transmit.
What do you need to do to set up video collaboration?
Adding video capabilities to your remote workforce enables your employees to continue to have face-to-face meetings, even if the other face is on a screen. While not a necessity, adding video improves communication because it adds nonverbal communication back into the conversation.
1. Video enabled devices
To add video to meetings, you’ll need the appropriate hardware. Here are a few of your options:
Option 1: Home office video phone
Examples of this include a video-enabled desk phone (Cisco 8845 video phone), a touchscreen video phone (Cisco Webex DX80), and an external monitor (Cisco Webex Desk Pro).
Option 2: Laptop webcam
Most new laptops come with integrated webcams. If they don’t, you can purchase external webcams for your employees to connect to their laptop or desktop. Once you configure each user’s laptop as a softphone, they’ll be able to make video (and audio) calls from their primary work devices.
Alternative: Smartphone
With this option, you’re able to reimburse your employees for using a device they already have. As a bonus, your users are likely to always have this softphone within an arm’s reach.
2. Video conferencing platform
If you want to host or join conferences with video, your company will need to establish which platform you’ll use to do so. Along with video sharing, you’ll also be able to share content, including documents, media, and screens.
Security requirements for your remote workforce
Regardless of where your employees are working, they are your biggest vulnerability.
This vulnerability is magnified with a remote workforce since you don’t have control over their home network. However, you can implement hardware, software, and policies to continue to protect your assets while your employees are remotely accessing your company network.
What do I need to implement/install to provide cybersecurity?
1. Anti-spam
Anti-spam protects your email by flagging potentially malicious emails that could compromise your users’ endpoints as well as your network. 
2. Antivirus
Antivirus software protects your computer systems from a variety of malware. Traditional antivirus relies on a known database of existing threats (signature-based) to identify malicious activity, but next-generation antivirus, on the other hand, incorporates artificial intelligence and endpoint detection and response to identify and stop malicious threats.
3. DNS Security
DNS security tools identify unsafe domains and then alert and prevent users from accessing suspected hijacked or malicious domains.
4. Firewall
A firewall sits between a local network and the Internet and controls the incoming and outgoing network traffic to prevent malicious traffic from entering the local network. For remote users, firewalls also can create network segmentation and keep business traffic separate from other home users.
5. Intrusion prevention system
This layer of security acts as an alarm system. Intrusion prevention systems analyze what is happening on your critical security systems, logs suspicious or anomalous activity, and finally blocks and reports it to the network administrators.
6. Multi-factor authentication
Multi-factor authentication protects your IT assets by requiring an additional layer of login security. You’ll need to enter your password, and a code provided by the multi-factor authentication application you use.
7. User education
Since users are your biggest vulnerability, the most effective security measure you can take is educating them on how to identify malicious or suspicious web addresses and emails. This way, your endpoint protection acts as a back-up instead of your primary means of protection.
This also includes reminding employees not to share corporate assets with family or friends. For example, don’t let your kids use your company device to play games or download other applications.
8. VPN connection
We already listed a secure VPN connection on this checklist, but it bears repeating since this is also a security measure to allow safe access to company applications.
Transitioning to a remote workforce
For many companies, they’ve already gone through a few of these steps and have some level of remote capabilities for at least a couple of employees.
The good news is even if your company has never had a remote employee, you likely have pieces of the technology already in place to transition to a remote workforce.
For connectivity, you don’t necessarily need to implement a secure Internet connection or increase your bandwidth. If you’ve had any remote employees, you likely already have the infrastructure to set up more VPN and VDI or RDS connections.
For collaboration, if a phone system is already in place, you just need to make sure you’ve set up and/or configured the capabilities that allow you to offer audio and video collaboration to your remote workforce.
And for security, you should have multiple layers of protection already in place to protect your assets. When setting up a workforce, you should be checking they extend to remote users and you have a way to separate home activity from business activity.
For an easy way to keep track of the remote technology you already have and what you need, download our free remote work checklist.